When enterprise security teams need to expand visibility into critical platforms, data ingestion playbooks can make the difference between guessing and knowing. Our latest release focuses on MuleSoft–the widely used API management platform–bringing its audit and sign-in logs directly into Microsoft Sentinel for streamlined monitoring, alerting, and investigation.
Why We Built It
Microsoft Sentinel includes a native MuleSoft connector, but in practice some organizations encounter deployment issues that block adoption. At the request of several customers, we developed and tested an alternative connector that integrates cleanly and works consistently in production.
The goal was simple: give security teams a fast, reliable way to collect MuleSoft audit and sign-in data without diverting weeks of engineering time to troubleshooting.
What It Does
The playbook ingests MuleSoft audit and sign-in logs into Sentinel, enabling security teams to:
- Detect suspicious logins, such as sign-ins from unusual IP addresses or geographies
- Identify anomalous actions within MuleSoft that could indicate account compromise
- Correlate MuleSoft activity with other data sources for richer investigations
- Build analytics rules to trigger alerts on defined behaviors
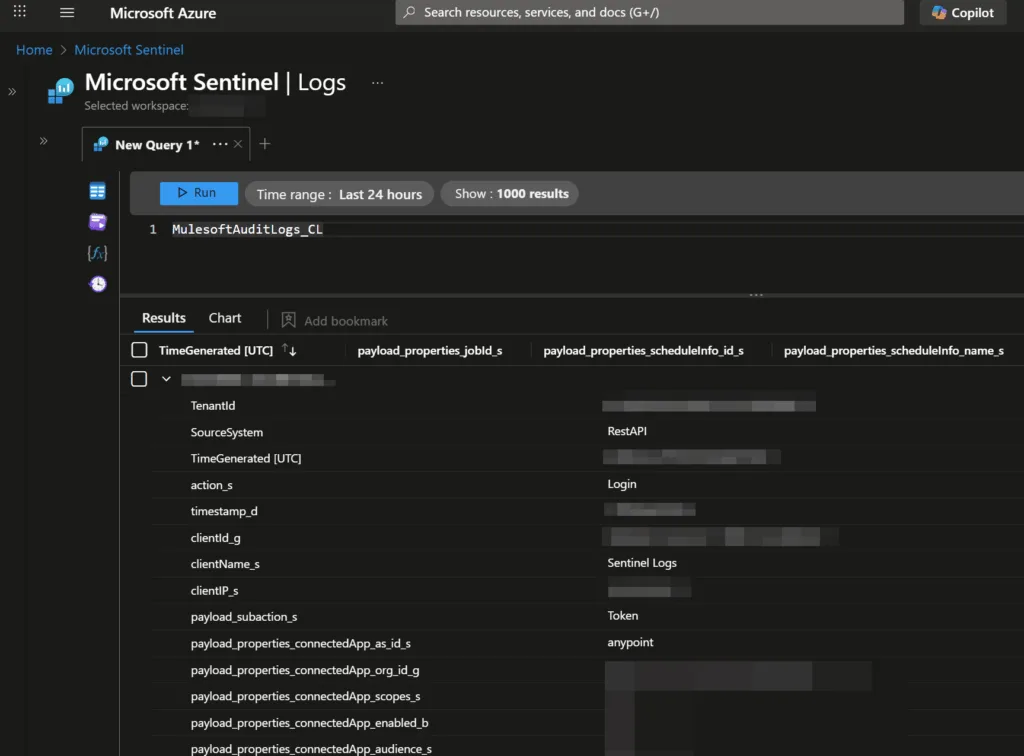
With API tokens, schemas, and integrations often stored in MuleSoft, any compromise could give attackers a broad pivot point into connected systems. Capturing and analyzing these logs is a direct way to reduce dwell time and limit impact.
How It Fits into Your Operations
This is a straightforward ingestion playbook–not an orchestration or response workflow–so there are no downstream dependencies on other data sources or tools. Once logs are flowing into Sentinel, security teams can immediately start writing analytics rules and hunting queries to match their operational priorities.
For enterprises already using Microsoft Sentinel as a central aggregation point, adding MuleSoft logs closes a visibility gap without introducing additional complexity. The process is repeatable, reliable, and quick to deploy.
Access and Deployment
As with all our community playbooks, we’re releasing this openly for any security team to adapt and use. You can find the full deployment guide and playbook in our public GitHub repository.
About Accelerynt
Accelerynt helps enterprise security teams enhance visibility, reduce operational drag, and build agile security operations using Microsoft Sentinel. Our ingestion and automation playbooks are developed from real-world customer needs, tested in live environments, and shared openly to help teams move faster with confidence.


