Security operations teams can’t act on what they can’t see. That’s why ingesting DataDog logs into Microsoft Sentinel is essential for building a unified, actionable view of your environment. Our newest playbook focuses on DataDog—an observability platform widely used for infrastructure and application monitoring—by delivering its logs directly into Microsoft Sentinel for centralized analysis and alerting.
Why We Built It
Many of the enterprises we support depend heavily on DataDog for visibility into system performance and operational health. When they attempted to integrate DataDog logs with Microsoft Sentinel, the available connectors, both native and marketplace, often fell short in terms of flexibility or reliability.
To address this, we developed a custom ingestion workflow that ensures DataDog logs flow into Sentinel without disruption. This approach lets analysts view operational telemetry side-by-side with security data, shortening investigation times and enabling a more complete understanding of potential threats.
The goal: give security teams a dependable way to connect performance and security insights without losing time to integration headaches.
What It Does
The playbook collects log data from DataDog and ingests it into Microsoft Sentinel, enabling security teams to:
- Monitor application and infrastructure anomalies in the same context as security alerts
- Detect operational patterns that could point to security issues, such as sudden configuration changes or unexpected resource activity
- Cross-reference DataDog events with other log sources to enrich investigations and improve triage
- Build analytics rules that trigger alerts when specific thresholds or conditions are met
Because DataDog often captures granular metrics from production systems, bringing that data into Sentinel adds depth to threat detection and accelerates the time from observation to response.
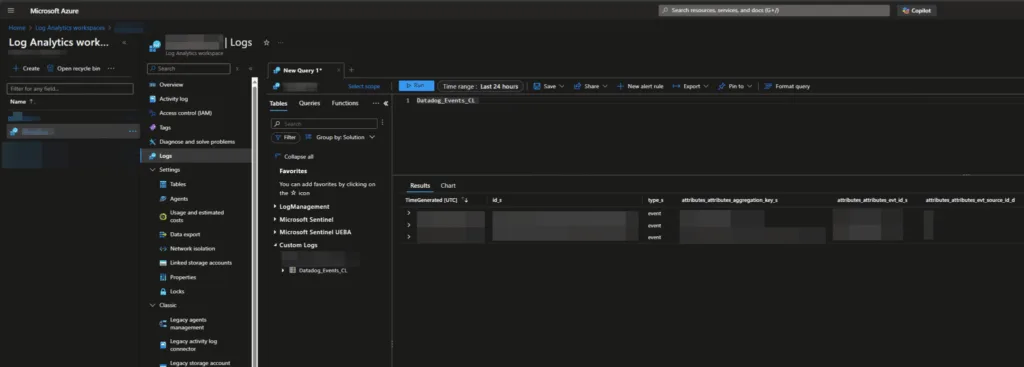
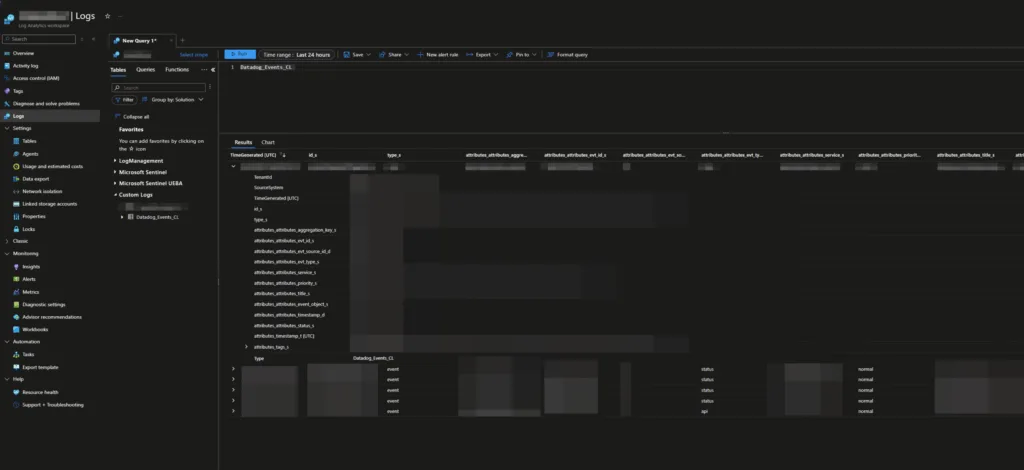
How It Fits into Your Operations
The playbook is designed for straightforward ingestion, meaning it won’t introduce complicated dependencies or overhaul your existing workflows. Once DataDog logs are flowing into Sentinel, analysts can immediately put them to work—whether that’s running targeted KQL queries, enriching dashboards, or creating rules that tie operational signals to security alerts.
For teams already using Sentinel as their main event aggregation and correlation layer, bringing in DataDog telemetry creates a bridge between infrastructure health and security posture. Instead of toggling between tools, your team gains a consolidated lens on performance and protection.
Access and Deployment
We’ve published the full deployment steps and playbook in our public GitHub repository. You can clone it, adapt it, and put it into production in a matter of minutes. No proprietary dependencies, no long configuration cycles—just a clear path from download to ingestion.
About Accelerynt
Accelerynt works with enterprise security teams to improve visibility, reduce operational bottlenecks, and enable agile security operations using Microsoft Sentinel. Our ingestion and automation playbooks are built from real-world requirements, validated in active environments, and shared openly to help teams act faster and smarter.