Accelerynt customers utilizing Microsoft Sentinel can now manage incident reporting via the PagerDuty Dashboard.
PagerDuty’s status dashboard provides technical responders, business responders, and leaders a live, shared view of system health to improve awareness of operational issues.
With Accelerynt and PagerDuty working together, you can streamline incident reporting process and get the information you need to respond quickly and effectively.
Benefits of Using Sentinel Push Notifications and PagerDuty Together
When you integrate Accelerynt’s Sentinel Push Notifications with PagerDuty, you get several benefits including:
- Easy access to critical incident details for fast remediation
- Linkage to powerful dashboards that provide transparency into the incidents
- Streamlined collaborative triage and incident management functionality
With all your alerts in one place, you can quickly and easily identify incidents, share them with your team, and monitor your overall system.
This will help reduce response time, improve your overall efficiency, stay ahead of potential threats, and allow your team to work together to resolve incidents quickly and effectively.
How to Get Started
This playbook is intended to be run from a Microsoft Sentinel incident.
It will create a PagerDuty event with the related Microsoft Sentinel incident and entity information.
Requirements
The following items are required under the template settings during deployment:
- A PagerDuty integration key
Setup
To Create a PagerDuty Integration Key:
Log into your PagerDuty account at https://app.pagerduty.com/.
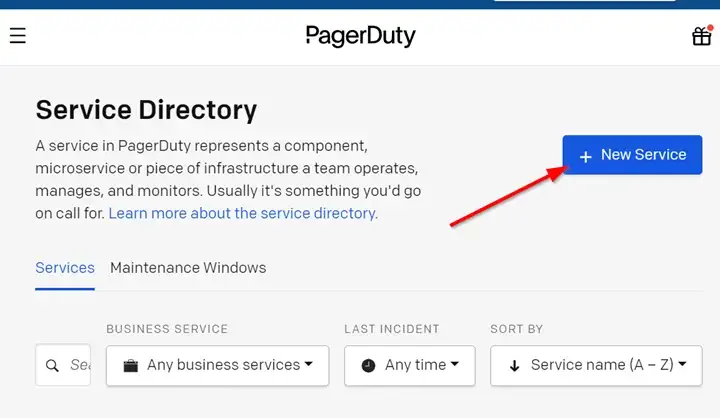
Under the “Services” menu option, select “Service Directory”.
From the page, click the “New Service” button.
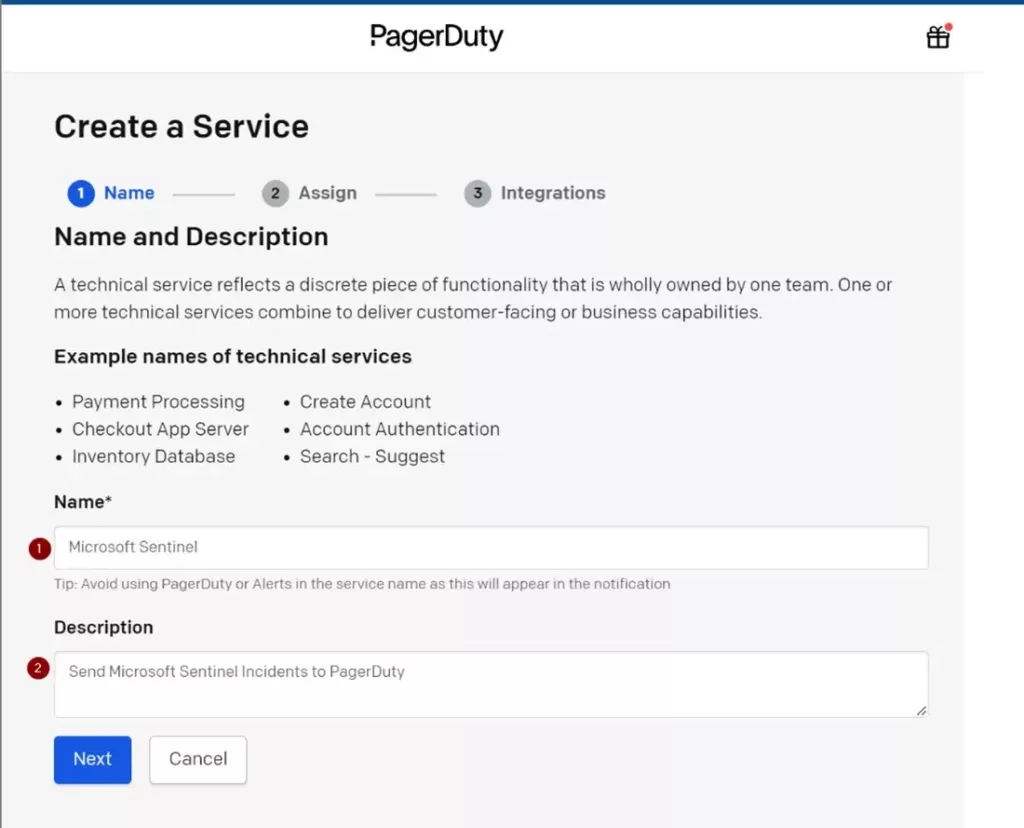
Add a Name and optional Description like the following:
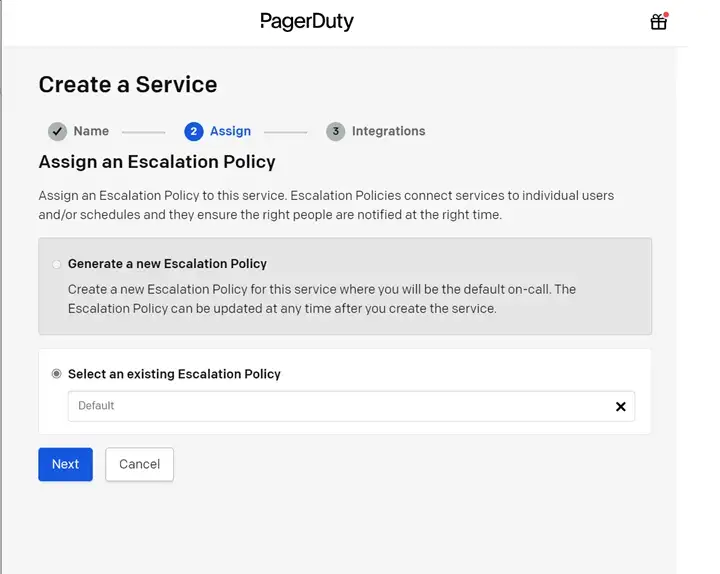
Select an escalation policy for your service.
In this example, the default is used.
There may be a step to select a noise reduction option for your service. The “Intelligent” option is recommended.
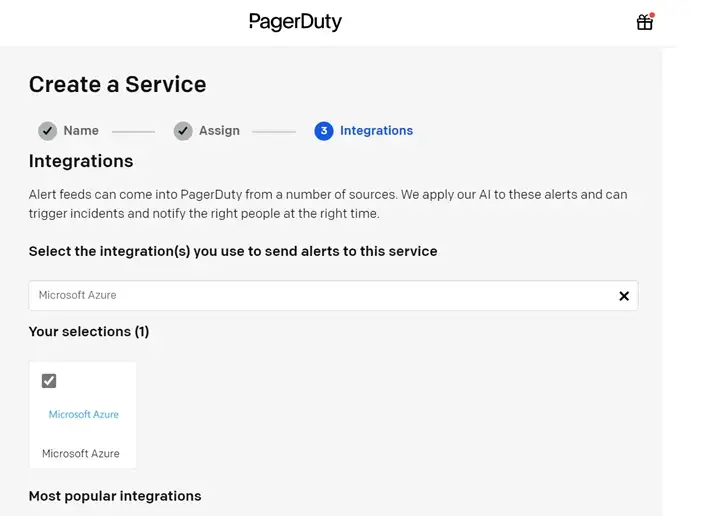
Finally, select the Microsoft Sentinel option under the Integrations section, then click “Create Service”.
You will be redirected to the service you have created.
Under the Integrations tab view, you will find your integration key.
This will be needed for the deployment of this playbook.
Deployment
To configure and deploy this playbook:
Open your browser and ensure you are logged into your Microsoft Sentinel workspace.
In a separate tab, open the link to our playbook on the Accelerynt Security GitHub Repository:
https://github.com/Accelerynt-Security/AS-PagerDuty-Integration
Click the “Deploy to Azure” button at the bottom and it will bring you to the custom deployment template.
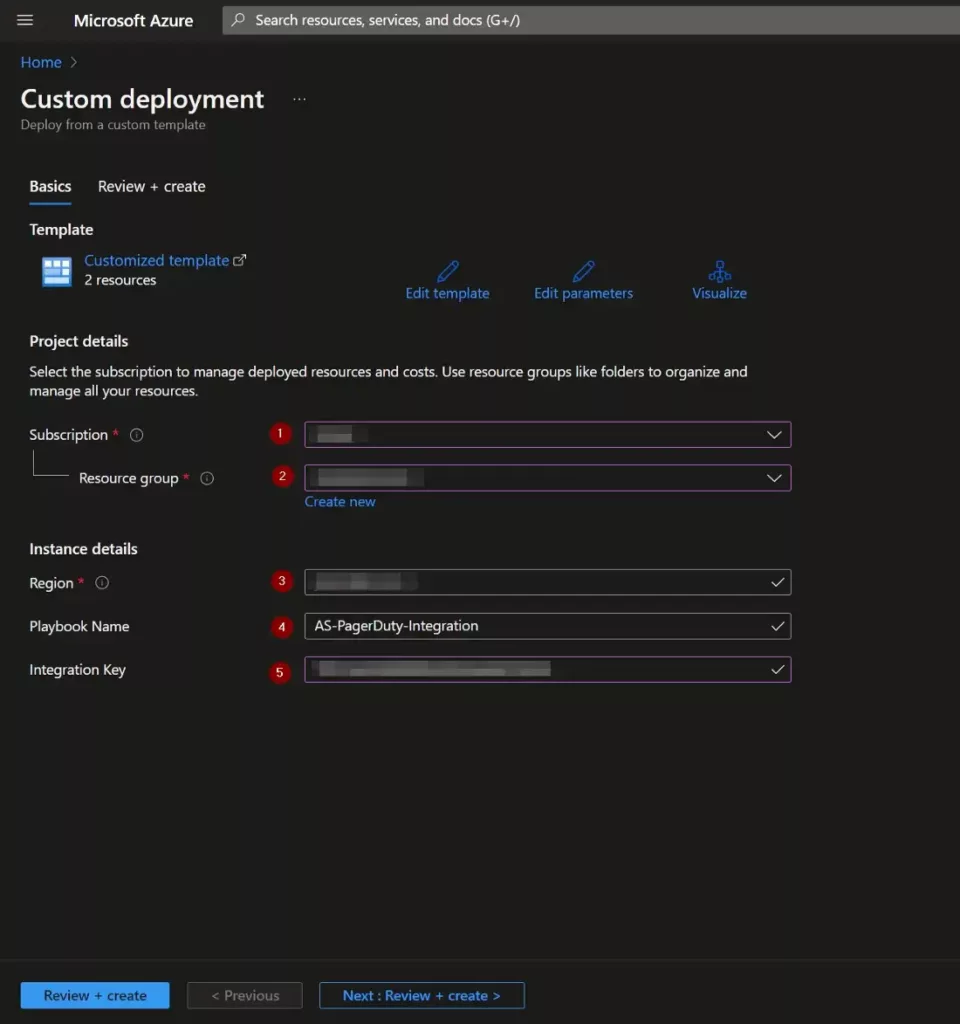
In the Project Details section:
- Select the “Subscription” and “Resource Group” from the dropdown boxes you would like the playbook deployed to.
In the Instance Details section:
- Playbook Name: This can be left as “AS-PagerDuty-Integration” or you may change it.
- Integration Key: Enter the value of the PagerDuty integration key created from the first section.
Towards the bottom, click on “Review + create”.
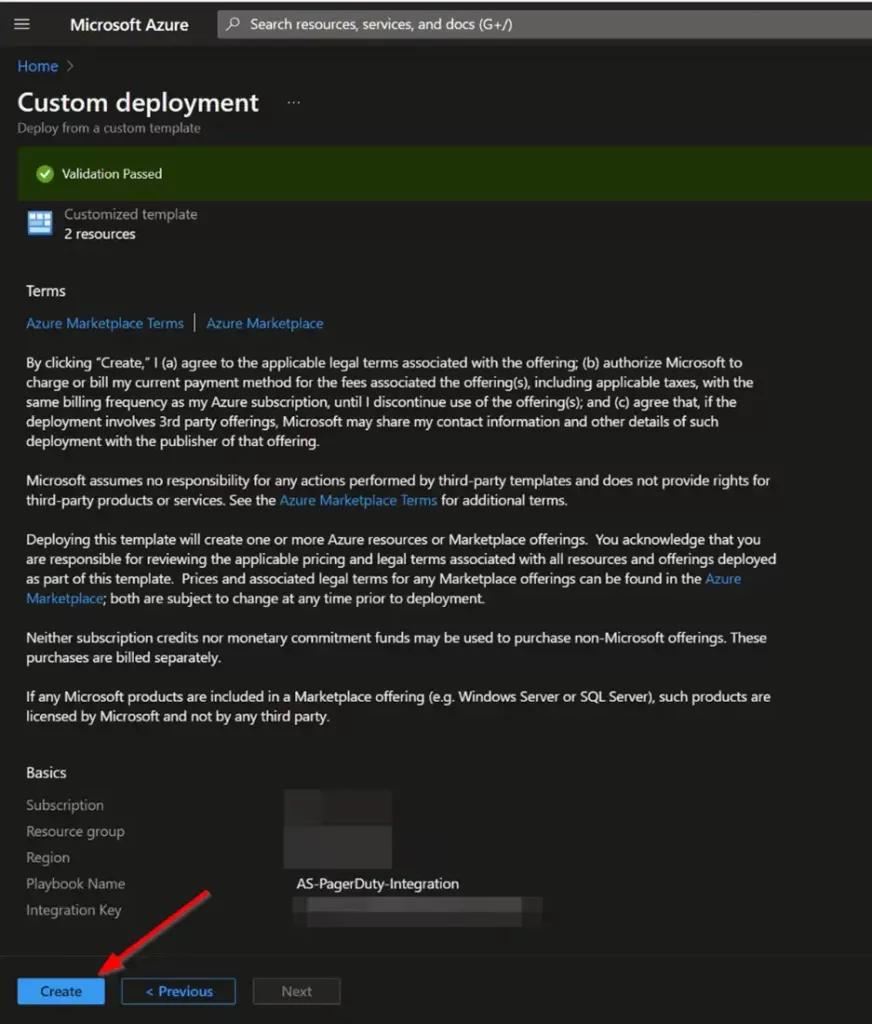
Once the resources have validated, click on “Create”.
The resources should take around a minute to deploy.
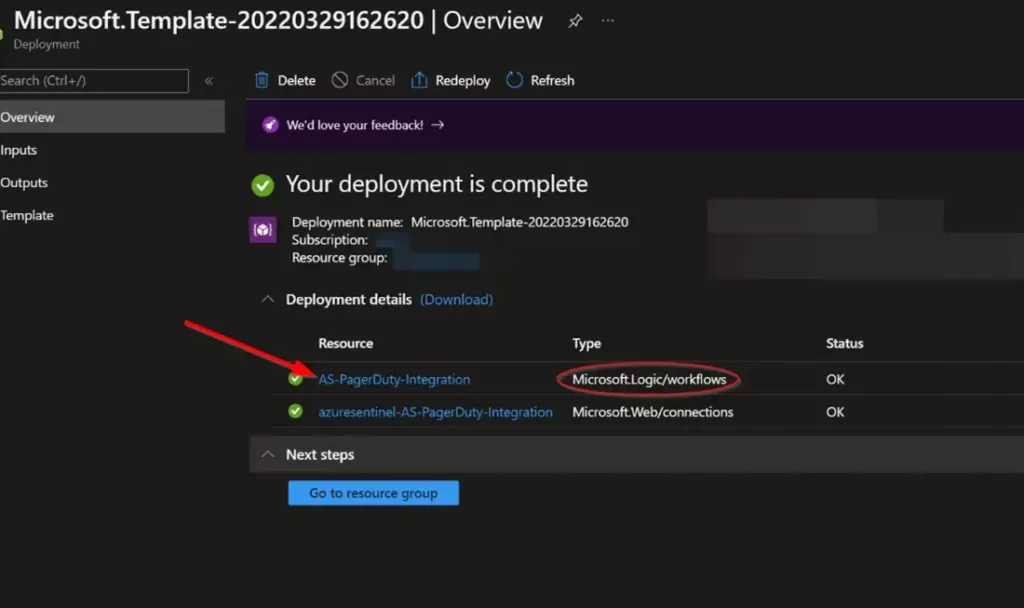
Once the deployment is complete, you can expand the “Deployment details” section to view them.
Click the one corresponding to the Logic App.
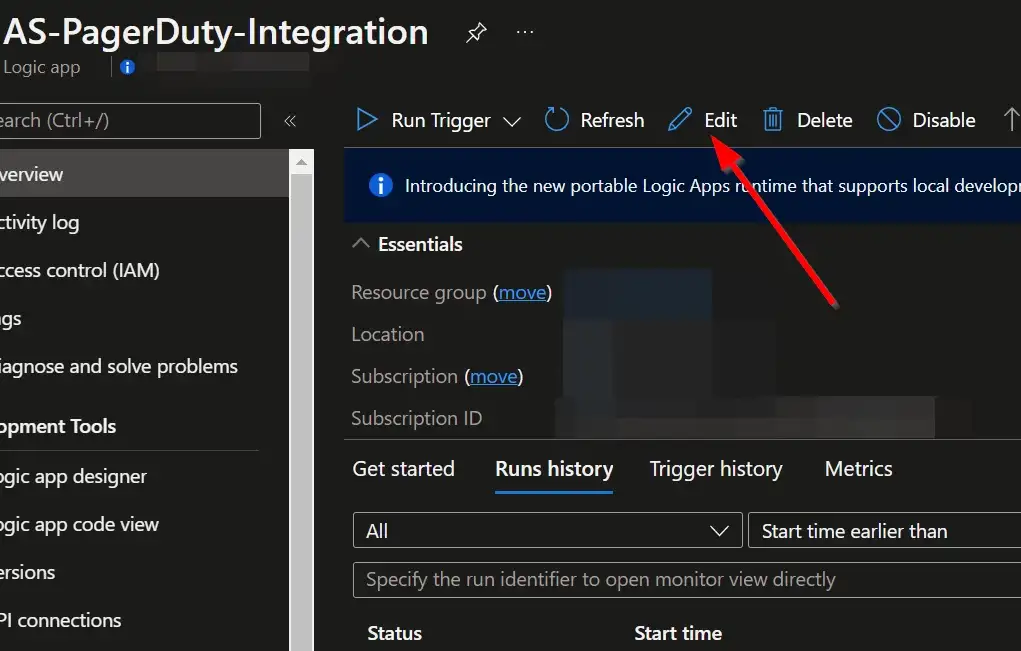
Click on the “Edit” button.
This will bring us into the Logic Apps Designer.
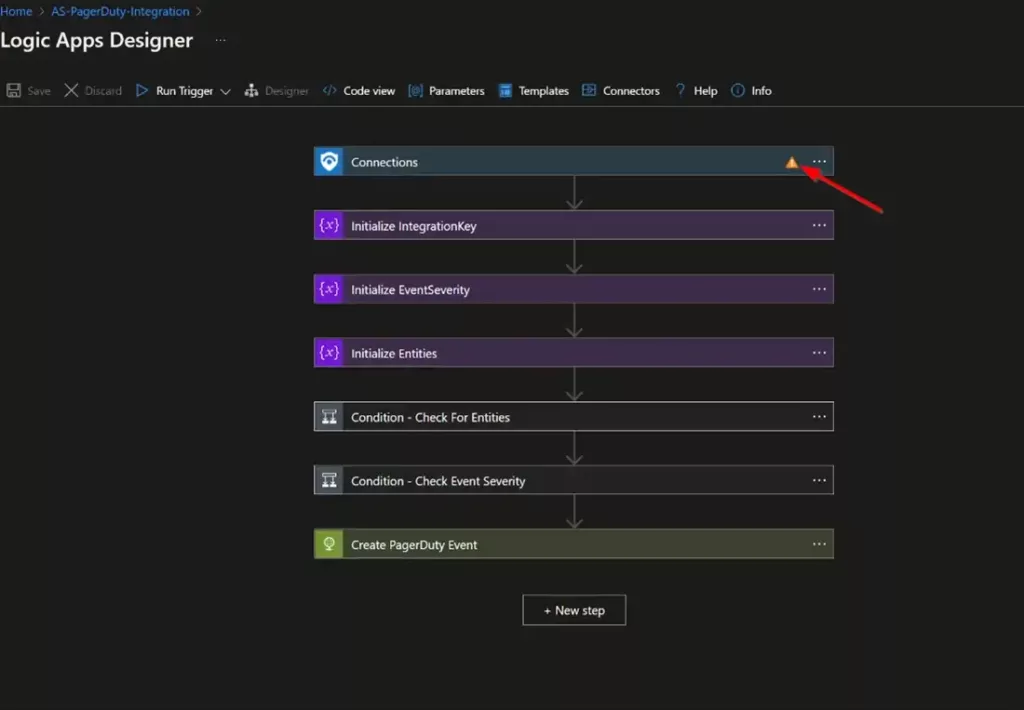
The first step labeled “Connections” uses a connection created during the deployment of this playbook.
Before the playbook can be run, this connection will either need to be authorized in this step, or an existing authorized connection may be alternatively selected.
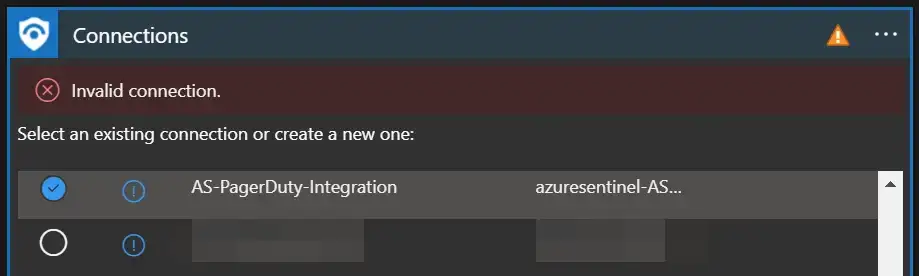
To validate the connection created for this playbook, expand the “Connections” step and click the exclamation point icon next to the name matching the playbook.
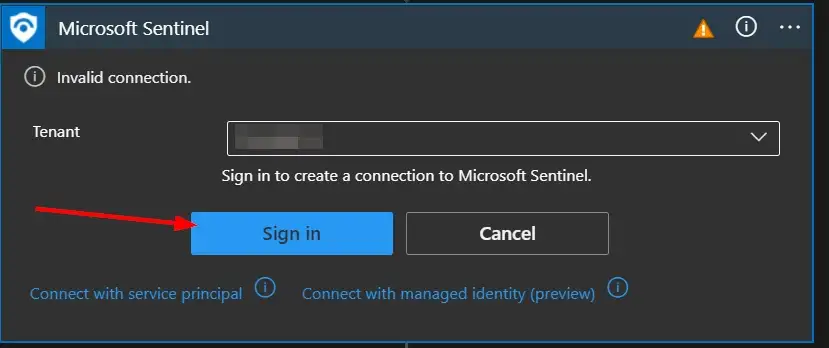
When prompted, sign in to validate the connection.
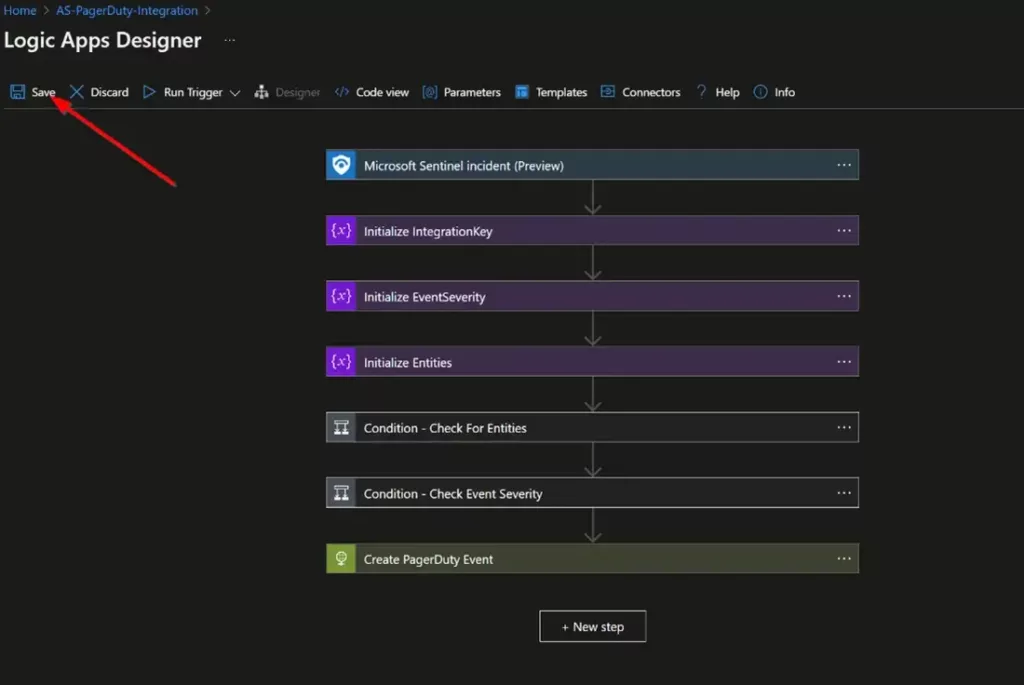
Once the connection step has been updated, click the “Save” button.
Running the Playbook
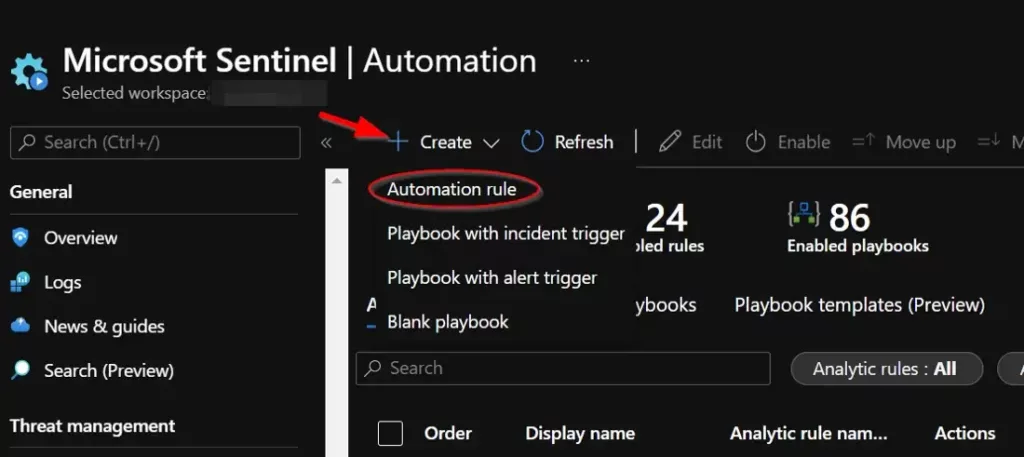
To run this playbook automatically on incidents in Microsoft Sentinel, navigate to “Automation” under “Configuration” in the left-hand menu.
Click the “Create” button and select “Automation Rule” option from the dropdown.
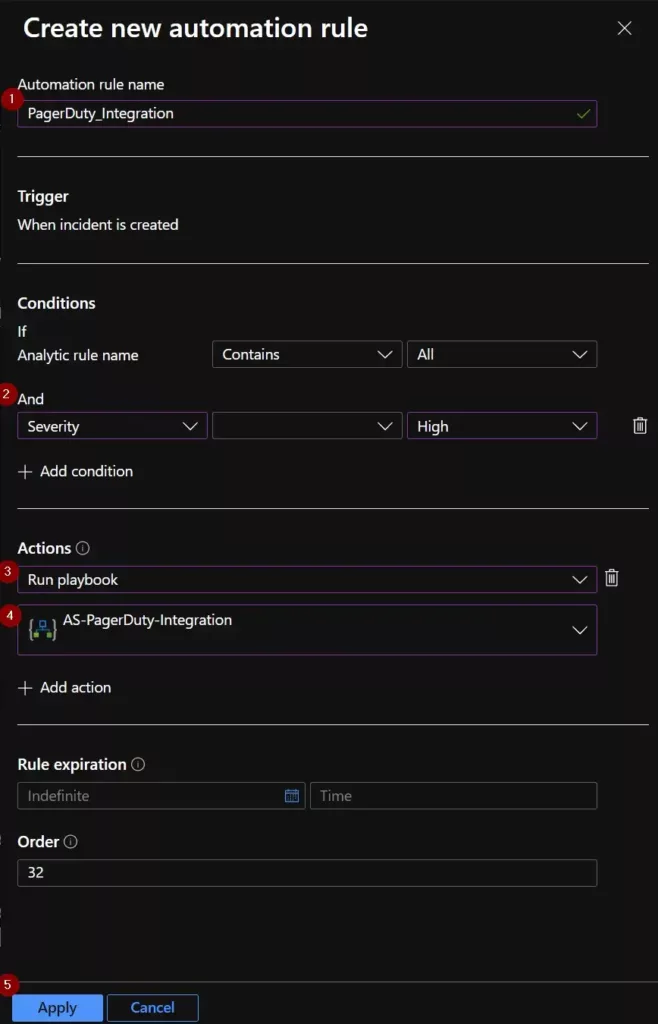
- Enter a name for the automation rule.
- Then stipulate the conditions for which you would like a Microsoft Sentinel Incident to be sent to PagerDuty. In the example below, criteria are set so that only incidents with high severity will be sent to PagerDuty.
- Select the “Run Playbook” option under the “Actions” section.
- Then select the name of the playbook that was just deployed from this page.
- Review the default values under the “Rule expiration” and “Order” section, then click Apply.
Once this saves, your new integration should run automatically.
Conclusion
With Accelerynt’s Sentinel Notifications now integrated with PagerDuty, Sentinel customers can experience quick and streamlined incident reporting.
This will help reduce response times and improve the overall customer experience.
If you are not already a customer of Accelerynt, contact us today to learn more about how we can help with improving your business performance.
Email info@accelerynt.com for more information.