In the fast-paced world of digital tech, every company needs to protect its data and assets – it’s no longer a choice but a necessity. This is where security architecture comes in. What is Security Architecture? Think of security architecture as your company’s security game plan. It’s the overall design and framework that protects your […]
Recently, a vast migration to the cloud has been occurring for on-premise ERP systems moving to cloud-based SaaS, AWS, or Azure-based ERP environments. Many CFOs and CIOs are pushing to accelerate their organizations to a more secure, accessible platform for their accounting enterprise resource planning (ERP) systems. And with the rapid increase in remote work, […]
Attackers are always refining the tools they use to improve the chances they can break through your defenses. Even small gaps can become a leverage point. And it doesn’t take much effort for the attackers to find the gaps — most of the attack tools these days are automatically scanning for changes, vulnerabilities, or other […]
Like it or not, the remote workforce is here to stay. Statistics show that employees say they are more productive working from home, and even before the global pandemic, there had been a 44% growth in the remote workforce over the past five years. In 2020, because of the pandemic, 88% of businesses worldwide mandated […]
Accelerynt customers utilizing Microsoft Sentinel can now manage incident reporting via the PagerDuty Dashboard. PagerDuty’s status dashboard provides technical responders, business responders, and leaders a live, shared view of system health to improve awareness of operational issues. With Accelerynt and PagerDuty working together, you can streamline incident reporting process and get the information you need […]
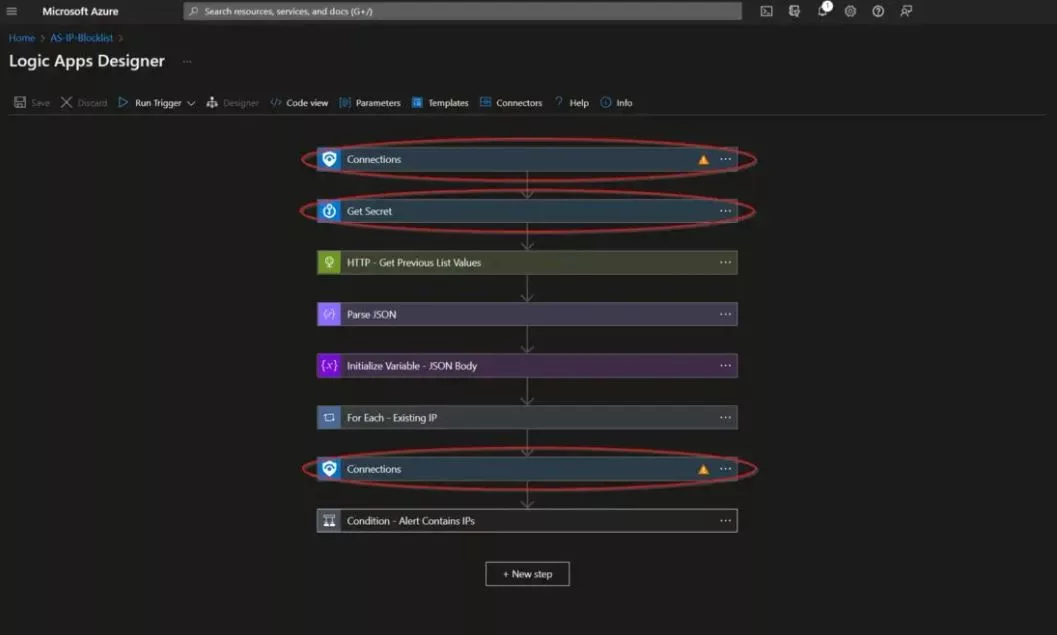
Imagine you’re responsible for security at a company that uses Azure Active Directory. One day, you receive a report of an attempted security breach. You need to act fast to protect your company’s data. With Accelerynt and Azure Active Directory locations, you can quickly and easily block the attacker’s IP address. This will help to […]